Another week, another hack(s). Once upon a time, the Mt. Gox hack was considered an earthquake. Nowadays, thefts of millions of dollars from crypto storage venues such as Youbit, Coincheck and Nicehash are just daily news. For crypto exchanges, wallets and mining pools cyber security weaknesses continue to be a major headache.
Discover credible partners and premium clients at China’s leading finance event!
Finance Magnates reached out to leading experts in the field of cyber security, with special focus on the crypto industry, to get their views on this.
The unbelievable numbers of users, alongside the enormous amounts of money that go through the exchanges, makes them a lucrative target for hacking. Hong Kong-based Binance, for instance, has more users than the population of its home state. Also, according to Coinmarketcap, the top 5 exchanges have a daily turnover of more than $1 billion (and in some cases closer to $2 billion).
One of the top 10 most targeted industries
“Crypto exchanges have and will more frequently become the target of criminal activity, given the inherent value of trading pairs stored on their platforms and the anonymous nature of trades assert. Hiding gains made from hacking events is relatively simple when compared to the traditional Fiat-based banking system,” says Damon Madden, a fraud consultant for ACI Worldwide.
This notion that is true for hacks is also relevant in the case of DDOS attacks. Recent research conducted by Imperva called 'Global DDoS Threat Landscape' reported that the crypto space was one of the most targeted industries (3.6% of all DDOS attacks, disproportionally high compared to other larger industries). “…in Q3 2017, we saw attacks targeting a relatively high number of cryptocurrency exchanges and services. This was likely related to a recent spike in the price of bitcoin, which more than doubled in the span of the quarter. As a result, bitcoin made the top-10 most targeted industries list, despite its relatively small size and web presence.”
Grave consequences
Hacks and other cyber-attacks are not new, but recently they began exacting a very heavy price from the crypto storage venues (and mostly exchanges). Youbit of South Korea, for instance, was forced to file for bankruptcy after being hacked twice. Japanese Coincheck is currently struggling to survive after a hack that caused it to lose ~$530 million of its costumers’ money.
In other, less reported cases, these attacks lead to other damages and expenses, such as client compensation, reputation damage, harm to servers, and more.
Vulnerabilities
So, what are the main causes of those hacks? According to Blockchain Graveyard, the blog of Ryan McGeehan, a former security director at Facebook and Coinbase, server breaches are the most dominant reason, while insider jobs are quite rare.
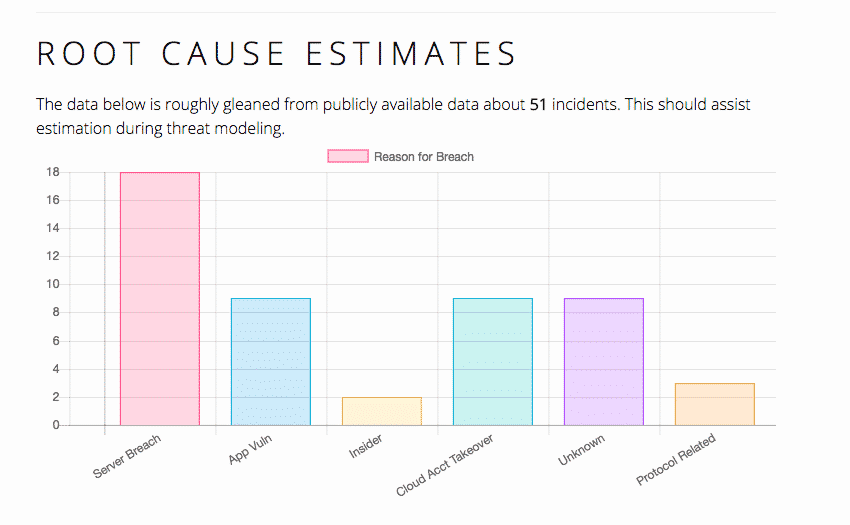
Source: Blockchain Graveyard
According to Michael Collins, co-founder and CEO of GN Compass in Calgary, Alberta, smaller exchanges are more perilous. “They don’t spend as much on security as the bigger exchanges which obviously makes them more prone to attacks. People like smaller exchanges because they can buy less popular coins at cheaper rates before they become more mainstream.”
Rick Deacon, the CEO of Apozy – a cybersecurity platform – continues along these lines and points at the rapid appearance of new exchanges, which don’t tend to mind security that much. “A lot of them are being hosted on cloud services (not inherently a problem) and developed with one thing in mind: trade coins quickly.
Another problem is lack of proper code review. While I haven't found or exploited any particular problems, this often leads to web security vulnerabilities.”
In his opinion, this opens them up to a variety of attacks, including “session hijacking, client-side exploitation, and back-end vulnerabilities.”
Ben Goodman, founder and CEO of 4A Security & Compliance, adds: “Specific security controls including access controls around elevated account privileges are among the vulnerabilities exploited, but this is not a problem that is unique to crypto exchanges.”
Extremely easy to mimic
Another major problem that crypto storage venues face is phishing, on the level of both user accounts and administrators.
“While there is not a lot of information on who perpetrated the recent hacks of cryptocurrency exchanges, now totaling over $1 billion, we do know that in some cases, internal credentials were phished and used to access administrative accounts, which is a fundamental level of security that some of these organizations are simply leaving vulnerable,” Goodman notes.
Deacon elaborated on the ease of hijacking one’s identity by phishing: “It's extremely easy to mimic an exchange and steal credentials from users. Given the sheer volume of funds going in and out, there's a lot to be stolen. Attackers will setup or hijack sites, send out false emails, and collect hundreds of thousands of dollars before anyone can notice.”
Trojan horses
Scam coins are also a known way to rid users of their money. That is why exchanges should be extremely cautious upon onboarding new currencies. “Anyone can setup a blockchain asset, such as a crypto currency,” says McGough.
“Another area giving rise to crypto exchange attacks is how an asset is listed with an exchange. Listing a ‘premine’ blockchain asset, where the developer does not release crypto currency in a fair manner, on an exchange for the lowest possible value can trick consumers into buying the asset without ability to sell it, thus providing criminals an avenue to scam users of an exchange.”
Solutions
According to Madden, the exchanges must be proactive to make sure that the trust upon which blockchain technology is built isn’t compromised.
“Every exchange has an obligation to their customers, the market and their peers to keep their platforms safe and free of financial crime. Trust is key in the digital world and while blockchain technology can provide this trust between two unknown parties, crypto exchanges and their controls are a weak link in the system.
Large publicized attacks, such as the Mt Gox incident, have impacted consumer adoption of the asset class, limiting investment in the underlying technologies with potential to improve delivery of goods and services across multiple industries including banking, supply chain and cloud based services.”
Cold storage
Almost all experts believe that the main precaution is to avoid storing cryptocurrency in a hot wallet.
“When using any exchange (especially smaller, more obscure ones) never leave your coins on the exchange wallet, always transfer them to a hardware wallet like trezor or ledger,” says Collins.
Akshay Mehra, co-founder and CEO of Genie ICO and Genie Crowdsourcing, continues along these lines: “The responsibility needs to be given back to the users via making transactions from user wallets faster and simpler, and moving away from exchange wallets. This is as much for user safety, as it is for the exchange operators’ risk minimization. The more funds that lie in an exchange’s wallet, the more liable is the exchange.”
Mike Jensen, Technology Lead at crypto commerce company Lantah, adds: “A hacker would have to drive to the place you are storing that wallet and then dig around until they find it. The likelihood of a successful theft is far lower when you've stored your coin in a cold wallet. It's also important not to keep addresses and keys in the same storage or transmission”.
Key management
Paul McGough, founder of Qwyit, says that the “key” for a secure exchange is the key management system. “Coincheck’s hack was most likely a direct assault on the private keys of the NEM coins. This is why a roll-back (or ‘hard-fork’) to a pre-hacked state of the exchange is not possible. And this is directly why the imposition of a proper key management system within both hot and cold wallets and exchange transactions can limit this type of attack – securing the private coin keys is essential to crypto-currency security.”
McGough adds that the multisig (multisignature addresses requiring multiple keys per transaction) is not necessarily the solution: “The 2016 $65M Bitfinex theft was the result of a successful multisig attack. The success of blockchain currency will need to demonstrate a new, robust layer of key management in any and every type of storage and transaction if it hopes to proliferate to other value assets, such as land and inventory management.”
He says that the best solution is “to have a more robust key management system – whether centralized or multi-layered – where the actual key structure can be interwoven into the brokering and/or clearing of transactions; whether this is in the platform, the wallet and/or the employee connections. This reduces, and can even eliminate, ‘stealing someone’s key’ and gaining root authority. Additional measures for person-to-key multi-factor authentication in realtime can also severely limit transaction fraud.”
Encryption
“In terms of the accounts themselves, exchanges should be implementing file-level encryption, so that data is unreadable at rest,” says Goodman. “Better key management can also prevent stolen accounts from being used. Also, role-based access controls along with segregation of duties, so that if an administrative account is compromised, the perpetrator will not be able to access elevated privileges. So in the event of a loss of credentials, you are not giving away the keys to the kingdom.”
Goodman advises: “Comprehensive monitoring and behavioral Analytics should be implemented so these entities could identify unusual activity on the network, and take appropriate actions before there is a breach.”
Due dilligence
Proper due diligence processes can assist in preventing internal attacks by users. But more importantly, there is a need for due diligence processes for the assets that the exchange handles. According to McGough, the cases of malicious use of assets such as currencies “highlight the need for robust customer due diligence processes to prevent false listings and the subsequent false, misleading purchase of such assets."
Authentication
Madden thinks that the authentication arrangements are crucial to protect user’s funds.
“Two-factor authentication practices are a must for all users within the system that limits the potential for account takeover. Tools such as Google Authenticator or SMS can provide base-level of authentication to protect users and their assets. Two-step verification should also have the user route through a secondary authentication channel to verify the transaction. This will limit and prevent malware attacks on exchange users through traditional banking Trojans, similar to the ones based on the Zeus family of Trojans.”
Regulation and enforcement
And after running through the various methods of preventing attacks and hedging the damage that they cause, it is important to stress that there is very little regulation imposed on the crypto-exchanges, if any. “The issue is that there is no oversight or regulatory authority to supervise the security at these new exchanges, like exist for most other financial institutions,” says Goodman.
Mehra suggests that crypto exchanges will be liable to similar regulations as other financial institutions: “As with the stock/ traditional exchanges, regulators will require that exchange operators keep aside funds to cover for fraud, inability to close out trades, and theft. There are no consistent rules on the operational risk requirements for exchanges, I expect these to change in the coming months.”