Kaspersky Lab, a Moscow-based cyber-security firm, has named cryptocurrency mining as its story of the year. It has found that attacks have gradually declined over 2018, but remain a major concern.
It should be noted that the information in the report only concerns countries with a considerable number of Kaspersky Lab clients.
What is Cryptojacking ?
Crypto-jacking has become a worldwide issue over the past year. This refers to cryptocurrency mining programmes being installed on computers unbeknownst to the users.
Cryptocurrency mining, for Bitcoin anyway, is a very CPU-heavy task, which is why most miners use dedicated machines instead of home computers. However, "it might be quite a while before the user notices that 70–80% of their CPU or graphics card power is being used to generate virtual coins," according to the report.
The threat is compounded by the ease with which these protocols can be designed - there are ready-made programmes available on the market - and by website plugins that begin running when the site is opened.
The problem is not confined to home computers either; the servers of large companies and government agencies have been regularly hit too.
A new business direction
Kaspersky reports evidence that mining software is an increasingly popular tool for botnets.
Botnets are networks of infected computers under the control of a hacker, which are being used to execute large-scale attacks. In the first half of 2018, mining protocols made up almost 5 percent of botnet downloads, compared to 2.7 percent in early 2017.
One traditional tactic of botnets is the 'distributed denial of service' attack, which is when large numbers of devices are used to jam a system by overloading it with requests, typically along with a ransom demand. Kaspersky registered a decline in this type of attack, which it says is the result of these networks switching to cryptocurrency mining instead.
For example, the 'Yoyo' botnet, which was first sighted in March 2010 and which has carried out hundreds of DDoS attacks worldwide, has "dramatically" lowered its rate of these attacks, but does not appear to have been disbanded.
Malware is being repurposed and becoming more sophisticated. For example, the 'Trojan-Ransom.Win32.Rakhni', which was first detected by Kaspersky in 2013, was a typical Trojan virus, and since 2018 has become a mining programme. It is disguised as an Adobe product.
Unmarked bills
The most popular cryptocurrency for this activity is Monero, market capitalisation $1.06 billion. It is designed to be anonymous and easy to mine; it is actually used charity organisations as a donation option on their websites, although in these cases users are given the option of performing the task. The coin has been banned by Japanese cryptocurrency exchanges because it is so ideal for illicit use.
In December 2017, users of Facebook Messenger in several countries found themselves generating Monero for an unknown recipient, and in March 2018, a flaw in a Linux plugin led to $75,000 worth of Monero being crypto-jacked from users in Japan, Taiwan, China, India, and the US.
Kaspersky says that "by some accounts" a total of $175 million worth of Monero has been earned in this way,or around 5% of all Monero currently in circulation.
Outside of the law
Interestingly, Kaspersky found no correlation between the legal status of cryptocurrency and frequency of attack. In the below chart can be found countries which have banned cryptocurrency, countries which have legitimised it, and countries in between the two.

Countries by share of mining attacks, January–October 2018. Source: Kaspersky Lab
Having said that, there is one area in which the law affects crypto-jacking; there is a clear correlation between the distribution of unlicensed software and mining attacks. The least affected countries were found to be the US, Switzerland and the UK.
The more I think about this the worse it becomes. Attackers had arbitrary script injection on thousands of sites including many NHS websites here in England. Just stop and think for a few moments about what exactly they could have done with that capability... ?
— Scott Helme (@Scott_Helme) February 11, 2018
Interestingly, mining software spread via hardware (USB drives) has increased annually since 2015. In 2016 this accounted for 4.2 percent of victims, in 2017 6.7 percent, and in 2019 one in ten.
Electricity prices, which are perhaps the main concern of cryptocurrency mining operations, are not taken into account by crypto-jackers, because they are not the ones paying for it.
Declining market
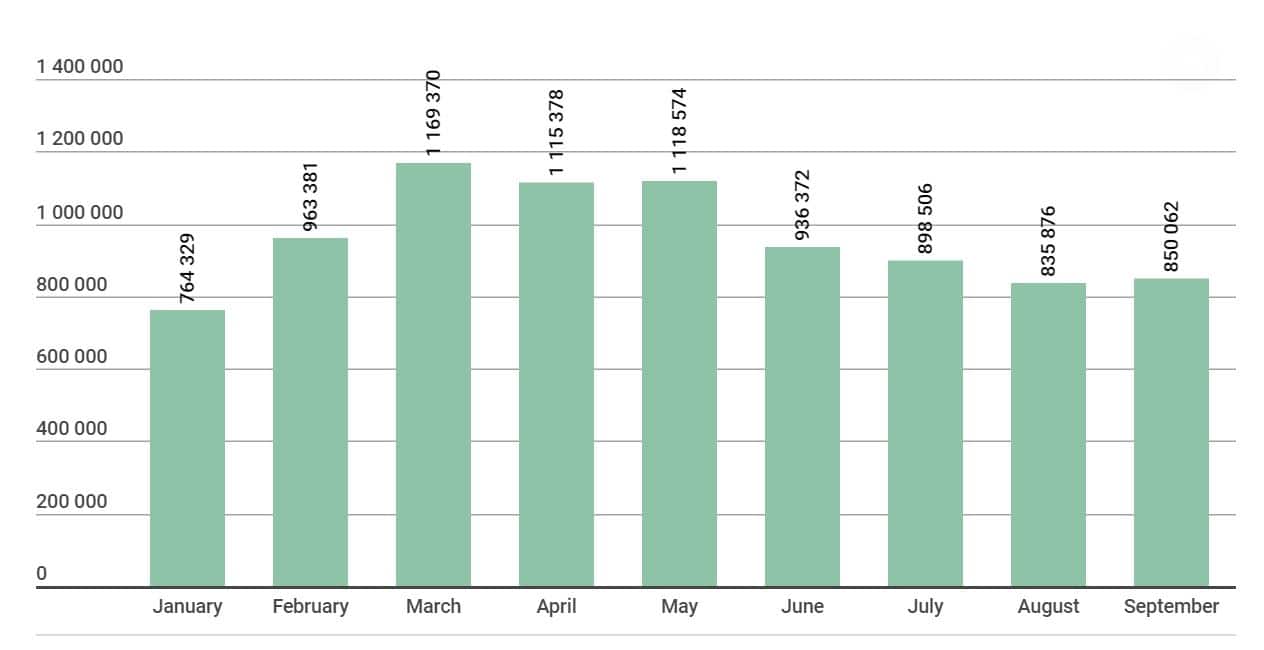
Number of unique users attacked, 2018. Source: Kaspersky Lab
As you can see from the above chart, attacks have declined. Kaspersky hypothesises that this reflects the general waning of interest in digital assets over the year.


















