What is the GDPR?
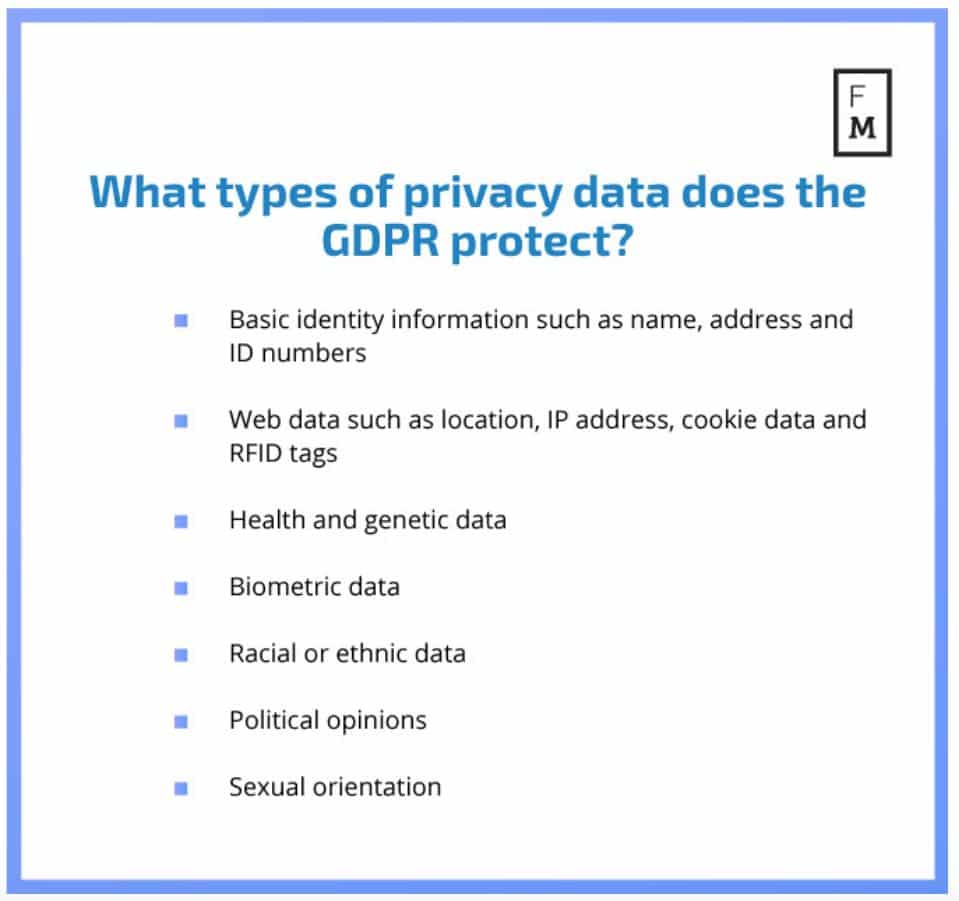
The GDPR, or General Data Protection Regulation , requires businesses to protect the private data of users and customers who are EU citizens. The GDPR applies to transactions that happen with companies based in the EU, as well as the exportation of personal data outside of the EU. The regulation will officially go into effect in May of 2018.
Essentially, any company that stores or processes personal data belonging to EU citizens has a new set of data protection standards to comply to, even if that company does not have a business presence within the EU itself.
The Consequences of Insufficient Compliance With the GDPR Are Steep
Under the GDPR, companies are required to provide a “reasonable” level of security. While the meaning of “reasonable” security isn’t defined clearly, the consequences for insufficient data protection and general compliance are steep.
Non-compliance offenses are divided into two categories: upper-level and lower-level. Lower-level offenses will result in a fine of either €10 million, or 2 percent of a company’s annual global revenue; upper-level offenses result in a fine of either €20 million or 4 percent of a company’s global annual revenue, whichever figure is higher.
The EU may be well-positioned to make a lot of money off of these fines. A report from Ovum revealed that 52-percent of companies do not believe that they will be sufficiently compliant with the new regulations; consulting firm Oliver Wyman predicts that the EU will collect €6 billion within the first year of GDPR enforcement alone.
Companies may also face greater threats from hackers who see the GDPR as a tool to Leverage ransom. Because the consequences of data breaches are so high, a hacker who gained access to personal data could hold it “hostage” for several hundred thousand or several million dollars, knowing that if the data is leaked, a company could face a minimum €20 million fine.
There is some saving grace--firms who do experience data breaches are required by GDPR to report the breach within 72 hours of discovery, and may be able to avoid fines this way. However, failure to report before the deadline has passed could mean serious trouble.

Are There Any Officially Approved Ways to Become GDPR Compliant?
The GDPR’s official website presents a list of firms that provide compliant data security solutions. However, there are only 2 companies in this list.
Indeed, there is more than one kind of technology that can be implemented to create a GDPR-compliant platform. With a diverse set of online industries, however, different kinds of technologies are more suited to different kinds of firms.
Becoming GDPR Compliant: Payment Card Industry Data Security Standards (PCI DSS)
For firms that need to process data as well as protect it, the Payment Card Industry Data Security Standards (PCI DSS) are known worldwide as obligatory set of policies and procedures for data protection related to credit, debit, and cash-card transactions.
PCI DSS mandates that companies maintain a secure network in which transactions can be conducted. Practically, this means that firms must provide adequate firewalls and encryption to prevent eavesdropping and hacking attacks.
Additionally, PCI DSS requires that “access to system information and operations should be restricted and controlled,” and that “networks must be constantly monitored and regularly tested,” among other requirements.
Tal Ron, Drihem & Co., Law Firm Believe that PCI DSS is the Key to GDPR Compliance
Throughout their experience, Tal Ron and Stephanie Attias have seen that both PCI DSS and the GDPR aim to ensure that companies secure their customers and users' personal data. The main difference between the two is that PCI DSS establishes a set of controls to keep the cardholder's data secure, while the GDPR focuses on securing European residents’ personal data.
However, according to Tal and Stephanie PCI DSS can be seen as a tool to achieve part of GDPR compliance. Indeed, Article 25 of the GDPR relates to data protection by design and default, and states that logs must be kept for processing operations so that any access can be monitored and reviewed in case any unauthorised access or action takes place.
This requirement matches the PCI DSS requirement 10.6.1, which mandates a daily review of security events and logs to ensure the cardholder's data is appropriately controlled.
Therefore, according to Tal and Stephanie, by being PCI DSS compliant your company will already have part of the required technology and procedures in place to secure personal data. This will give you a significant advantage on implementing the data security controls required by GDPR and you will be able to use such a framework when implementing GDPR measures.
By all means, in order to make sure that you are developing a strategic approach to GDPR compliance, it is crucial for your company to obtain appropriate legal advice and partner with an organization that can help you address GDPR requirements via custom-made services.
Utilizing a service that upholds the PCI DSS standards will ensure that a company’s operations are GDPR compliant. One of the GDPR-compliant data security solutions that use PCi DSS practises is Leads Protection Systems (LPS), powered by payment technology provider Payneteasy. LPS’s platform is based on PCI DSS, and utilizes specialized firewalls to meet a diverse set of data security needs.
Besides, LPS was designed as platform capable of end-to-end encryption; from the moment that a user hands over their data, it is divided, encrypted, and store in an Amazon Private Cloud. Only the holder of the encryption key can access the data--no one else, not even LPS, can touch it.
Choosing a Service: What else should I know?
The key to staying in line with the GDPR statements and ensuring that customer and user data is protected is to know the answers to a few simple questions:
- Who has access to my company’s database?
- Who is using my company’s database?
- How is my database accessed?
- When is my database being used?
In any firm that has a lot of moving parts, keeping track of who, how, and when user data is essential - not only to protect data from hackers, but also from internal employees who may seek to maliciously sell data or otherwise use it for their own purposes.
Malicious insiders — including disgruntled IT staff, greedy techies, sacked employees, and IT staff working with third parties — could plant logic bombs or steal data. Uncontrolled administrative access is a potential security threat, jeopardising your business.
The GDPR requires that organizations ensure and demonstrate compliance with its personal data protection policies. Protecting personal data, in turn, requires complete control over privileged access — the foundational tenet of the GDPR.
For example, controlling privileged access requires you to restrict access to accounts based on job roles and responsibilities. This means that a service for data protection should provide you with full and flexible access management tools. As we told above, it is very important to build a strong hierarchical system providing the strict rules for all the employees on all the sensitive data.
Besides the access management, a company should have the option to receive an alert every time that suspicious behavior turns up within the system, this also meets GDPR requirement. As, being informed on the suspicious actions immediately, increases chances to prevent data loss.
For instance, a single employee who suddenly accesses 300 client contacts within an hour should be automatically reported to leadership forces. This protects data from being stolen from the inside, and gives a company virtually total control over its data.
One more thing to know: It is understood, that organizations are required to work with third parties such as vendors, business partners, and contractors for a variety of purposes.
In a perfect situation, you stay the only keyholder of your database, but quite often, third-party partners are provided with remote privileged access to the sensitive data. It is imperative that choosing a service you should be sure that privileged access granted to third parties is controlled, managed, and monitored.












